Tag: replay attack
Automatic Dependent Surveillance-Broadcast – ADS-B (Part I)
This content is a piece of our initiative to study security in aviation. All experiences and content developed by us will be available here on right moment. To start, we will understand a little about ADS-B.
ADS-B is one of technologies from NextGen Platform (Next Generation Air Transportation). NextGen is a initiative from FAA (Federal Aviation Administration) for enhance the current Air Traffic Control. The proposal promises a great operational gains, security and financial support for the entire chain of stakeholders involved in air transportation.
ADS-B technology is responsible for communication between aircrafts and between aircraft and air traffic control. This technology has been widely used in aircrafts and it will be mandatory adoption in the coming years (from 2020 US / Europe 2017).
This is a cooperative surveillance technology for tracking aircraft. Each aircraft determine your position via GPS. Every aircraft equipped with ADS-B will periodically send your location information, speed, altitude, identification and other details to ground stations and others aircrafts also equipped with ADS-B present in that area.
This technology will replace the radar as the primary method of surveillance to detect the position of aircraft worldwide.
Supposedly the ADS-B technology should increase safety in aviation by making visible aircraft in real time, exchanging information such as position and velocity, transmitted every second, but the current technology of ADS-B make use of broadcast transmission, in clear text ( without encryption or other security measures) using radio frequency (1090MHz – Modulation PPM).
ADS-B technology consists of two different systems that are ADS-B In and Out.
ADS-B Out
It is the basic level of ADS-B functionality. It’s basically all communication that is issued by the ADS-B aircraft.
ADS-B IN
The information reported by ADS-B Out (other aircraft) will be received by aircraft equipped with ADS-B In system. This functionality is intended to alert the crew about the traffic around you.
Understood the basics, let’s look under security optical…
First, we have the situation where the plane is sending uncontrolled information concerning that flight. This set of information is sent in broadcast, or for everyone. It does not require authentication and is not made any kind of control of the recipient and sender.
The signal sent by the ADS-B uses the 1090MHz frequency modulation Digital Pulse Position modulation (PPM) and Manchester code where a ZERO bit is encoded 01 and the ONE bit is encoded 10.
An ADS-B message contains 112 bits, for example:
Example message in BINARY format:
10001101010010000100000011010110001000000010110011000011 01110001110000110010110011100000010101110110000010011000
The same example in HEX format:
8D4840D6202CC371C32CE0576098
The table below shows the bit organization of the message.
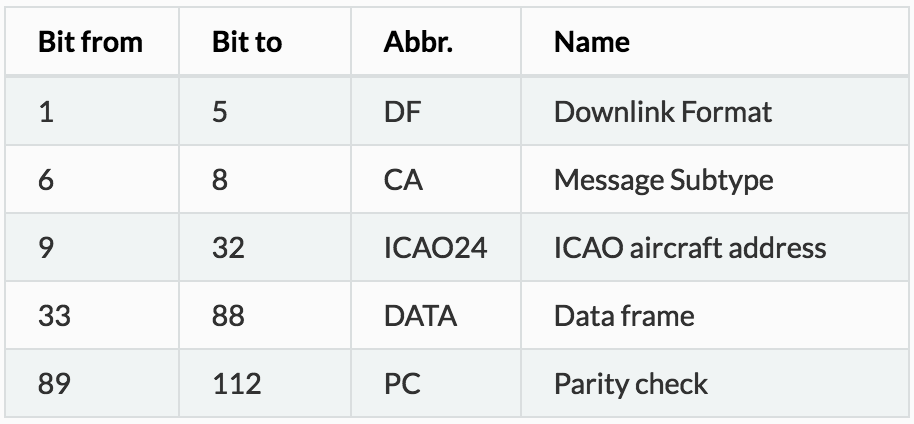
In a future opportunity we will detail every message part….
So far we understood that ADS-B from every airplane will be emitting the bit sequence shown above approximately 2 times per second.
Sites like FlightRadar and FlightAware uses radio receivers around the world, collaboratively, to capture the ADS-B information of the aircrafts and centered in a friendly way on the map showing the vast majority of flights flown in the world.
Illustrating how the tracking sites of ADS-B aircraft:

The ADS-B waveform can be observed in following images:
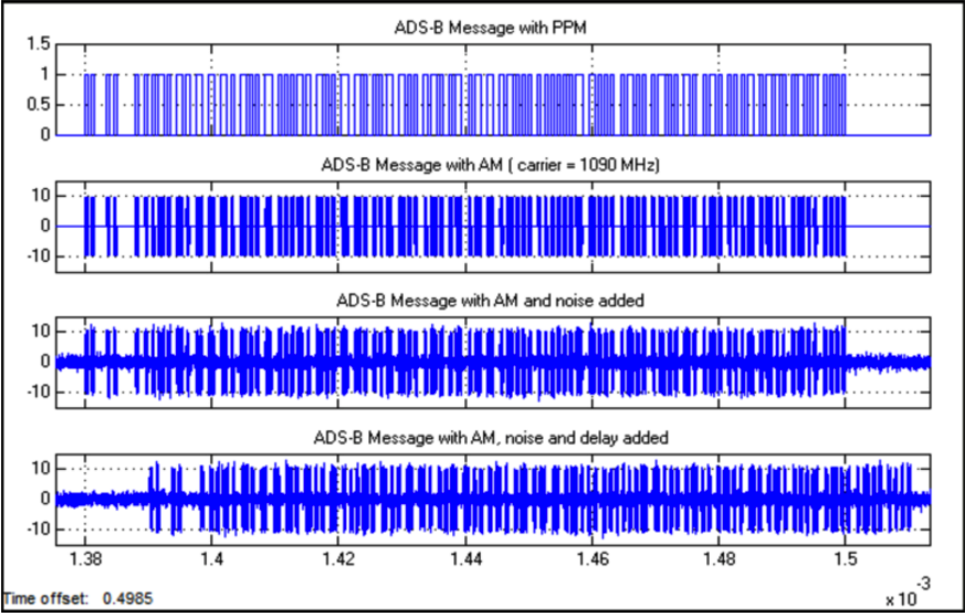

This is the first content, introduction to ADS-B technology. In the next content we will discuss more about the decoding and show how you can capture the information of the aircraft in its viewing area. Only after that we can have a view of the risks of ADS-B technology…
Think how dangerous a Replay Attack could be in aviation scenario.
to be continued…
Replay Attack – Doorbell
Recently I bought a low cost wireless doorbell so I decided to analyse the RF communication and reproduce a replay attack.
To accomplish the attack I used an Ettus USRP2 N210 SDR (Software Defined Radio), a Voye wireless doorbell and GNU Radio.
The replay attack (also called as playback attack) is simple and very interesting attack, it works by simply recording a signal and then rebroadcasting it once it used a “fix code” signal to activate the doorbell.


GNU Radio
GNU Radio Companion (GRC) is a graphical tool for creating signal flow graphs and generating flow-graph source code.
More info: http://gnuradio.org/redmine/projects/gnuradio/wiki/GNURadioCompanion
Identifying the signal
Usually doorbells operates at frequencies of 433Mhz (Europe) or 315Mhz (America), it was first noticed the frequency of 433Mhz in order to get signal but nothing was found. Analyzing the 315MHz frequency we found the signal from the doorbell transmitter.
We used GQRX to clearly identify the frequency:

Capturing the signal
We recorded the signal from the doorbell transmitter in GNU Radio into a RAW file.
We’re using 2e6 (2M) as Sample Rate and this value should be used in every step.

Opening this up in AUDACITY we can see groups of pulses making up a single button press and we can identify this is a OOK (On-Off Keying) Signal.

On zooming in to a button press, we can see these button presses are made up of similar looking groups.

Notice that we’ve exported 4 sequences because the receiver has a error rate and it needs to receive more than 1 package of bits.
We gonna export using the following configuration:

Transmitting the signal
Finally, the last step was to create a flow graph to transmit the raw signal isolated.
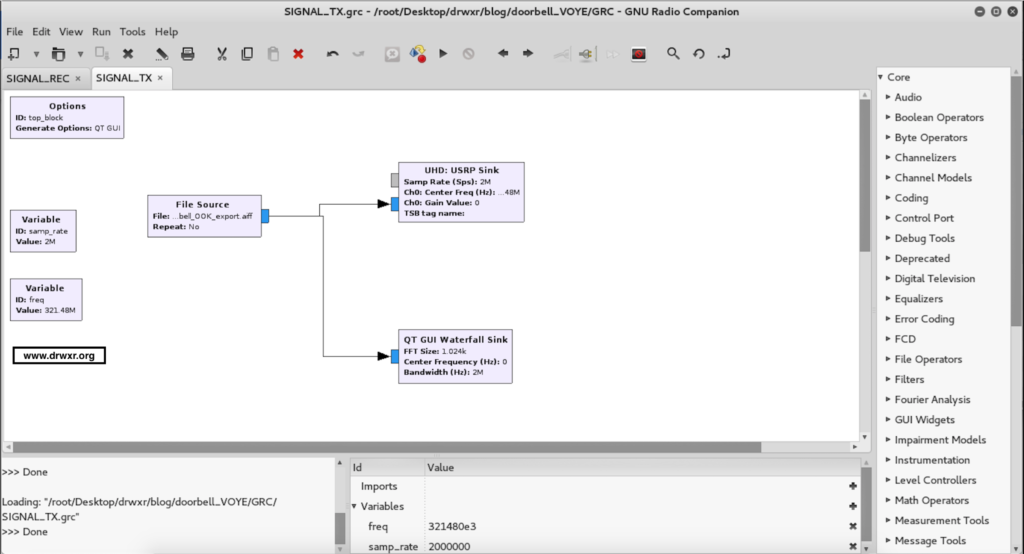
After executing the doorbell will ring…
Video of replay attack: