Tag: 433
Replay Attack – Doorbell
Recently I bought a low cost wireless doorbell so I decided to analyse the RF communication and reproduce a replay attack.
To accomplish the attack I used an Ettus USRP2 N210 SDR (Software Defined Radio), a Voye wireless doorbell and GNU Radio.
The replay attack (also called as playback attack) is simple and very interesting attack, it works by simply recording a signal and then rebroadcasting it once it used a “fix code” signal to activate the doorbell.


GNU Radio
GNU Radio Companion (GRC) is a graphical tool for creating signal flow graphs and generating flow-graph source code.
More info: http://gnuradio.org/redmine/projects/gnuradio/wiki/GNURadioCompanion
Identifying the signal
Usually doorbells operates at frequencies of 433Mhz (Europe) or 315Mhz (America), it was first noticed the frequency of 433Mhz in order to get signal but nothing was found. Analyzing the 315MHz frequency we found the signal from the doorbell transmitter.
We used GQRX to clearly identify the frequency:

Capturing the signal
We recorded the signal from the doorbell transmitter in GNU Radio into a RAW file.
We’re using 2e6 (2M) as Sample Rate and this value should be used in every step.

Opening this up in AUDACITY we can see groups of pulses making up a single button press and we can identify this is a OOK (On-Off Keying) Signal.

On zooming in to a button press, we can see these button presses are made up of similar looking groups.

Notice that we’ve exported 4 sequences because the receiver has a error rate and it needs to receive more than 1 package of bits.
We gonna export using the following configuration:

Transmitting the signal
Finally, the last step was to create a flow graph to transmit the raw signal isolated.
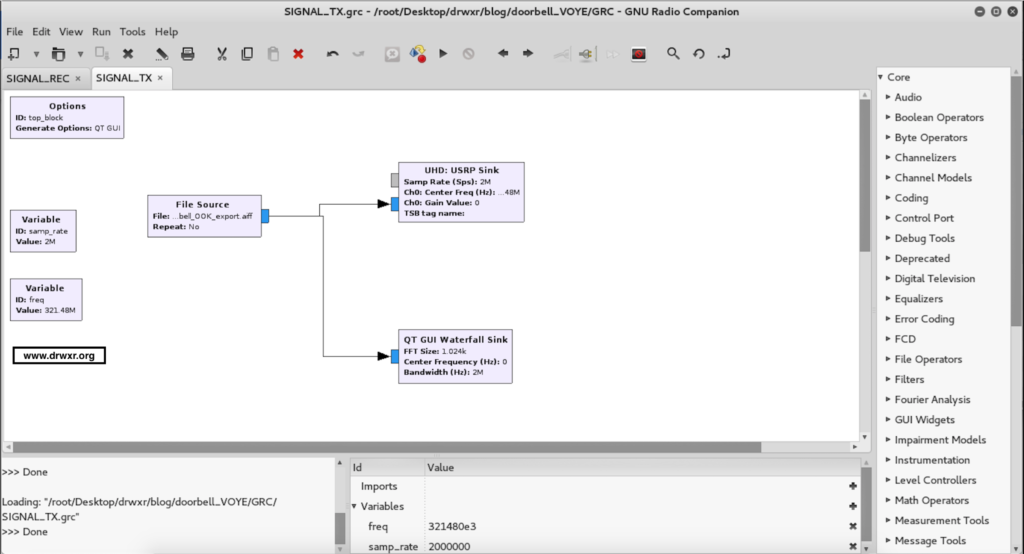
After executing the doorbell will ring…
Video of replay attack: